Security
Enhance the security of your exposed endpoints
At Qala, we take security seriously. To help protect your exposed Source URLs, we’ve developed a set of robust security features. You can also secure your Q-Flow Sources using IP whitelisting.
Let’s explore the available security options.
By default, no security features are enabled. We recommend enabling and configuring them to suit your requirements and safeguard your endpoints.
Authentication
To secure your Source URLs, you can enable authentication, which requires clients to provide valid credentials for access. The following methods are available:
- Basic Authentication
- API Key Authentication
- Bearer Token Authentication (JWT)
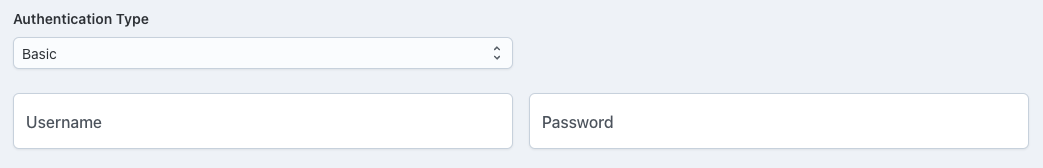
Basic Authentication
Basic Authentication requires clients to provide a username and password to access the Source URL.
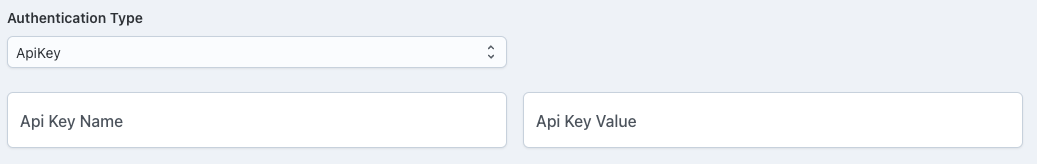
API Key Authentication
API Key Authentication requires clients to include an API key in their requests to access the Source URL.
Bearer Token Authentication (JWT)
JWT-based Bearer Token Authentication requires clients to include a Bearer token in their requests.
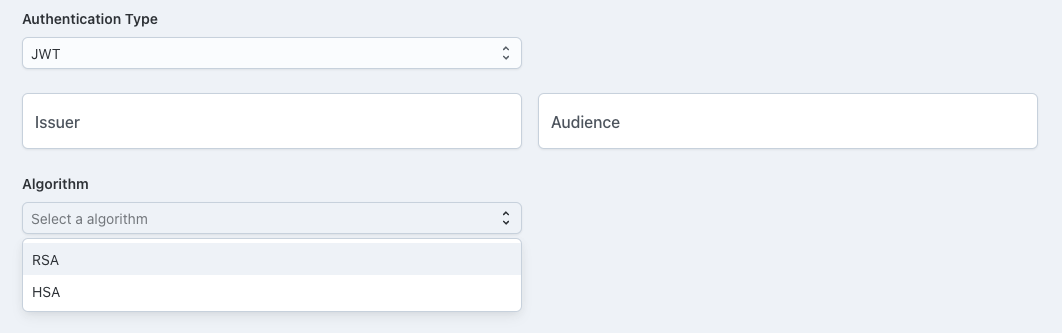
We support the following algorithms for JWT:
- HS256
- HS384
- HS512
- RS256
- RS384
- RS512
Depending on your requirements:
- RSA algorithms require a public key.
- HSA algorithms require a secret.
Choose the algorithm that best fits your needs and configure it accordingly.
IP Whitelisting
To restrict access to your Q-Flow Sources based on IP addresses, you can enable IP whitelisting. This allows only specified IP addresses to access the Source URLs.
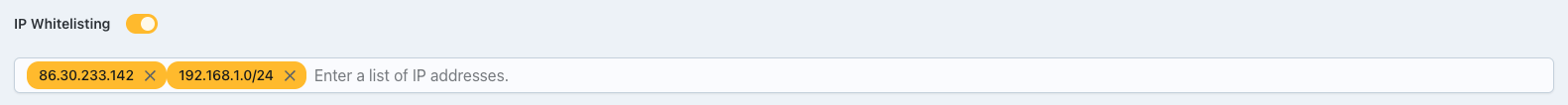
When enabled, you must supply valid IP addresses, ranges, or CIDR notations to grant access.
These features are designed to enhance the security of your endpoints. By enabling them, you ensure that only authorized users and systems can interact with your Q-Flow Sources.